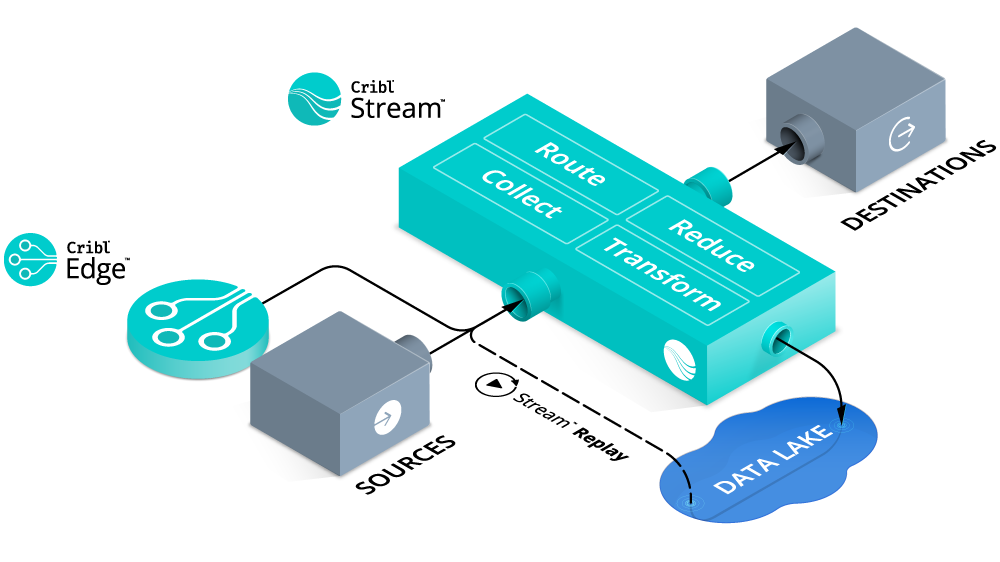
Do more with your big data
Discovered Intelligence is an award winning, global leader in data observability and security platform sales, service and development, with a reputation for delivering project excellence.
Sales & Licensing
Our premier levels of partnerships and fully certified sales team allow us to provide you with expert guidance and advice throughout the sales process, along with competitive pricing and value.
Professional Services
Our award winning, certified consultants, offer the highest levels of skills in the industry with with years of practical experience solving problems and delivering value to our customers.
Splunk App Development
We are a leading specialist in Splunk app development, offering white-label Splunk apps that integrate and report on your data sets in Splunk, and internal business apps that provide immediate value and intelligence.